After s4x21 cancellation and s4x22 3 month delay due to COVID, S4 was finally back from April 19th to April 21st 2022!
What is S4?
A 3 day conference, dedicated to ICS cybersecurity, held in Miami South Beach and organized by Dale Peterson.
- 3 stages: the Main Stage at the Fillmore theater, stage 2 and stage 3 mainly for technical deep dives at the ELV
- the Cabana Sessions around the Surfcomber pool to network, discuss with vendors such as Dragos, Nozomi Networks, Phoenix Contact, Keysight and many others but also get a copy of the book “Countering Cyber Sabotage: Introducing Consequence-Driven, Cyber-Informed Engineering (CCE)” signed by Andy Bochman and Sarah Freeman
- the Welcome Party at the Botanical Garden
This year, around 800 people attended the conference to create the future and Wavestone was there through my participation as both an attendee but also a speaker.
S4 actually started on April 18th with two specific events:
- The first ICS4ICS exercice (I will talk about that a bit later in this article)
- Women in ICS Security social event: more than 160 women attended the conference this year and it was great having the opportunity to meet incredible talents at a women only event; it was the first time such an event was organized at S4 and I hope not the last!
The talks started on April 19th and Dale kicked off the event with a keynote introducing this year’s theme: No Limits!
In this article, I am going to present some of my favorite talks.
If you are interested, all videos will be released in the next weeks on S4Events YouTube channel: https://www.youtube.com/c/S4Events/videos Here is the full S4x22 video release schedule: https://s4xevents.com/wp-content/uploads/2022/04/S4x22-Video-Release-Schedule.pdf Stay tuned!
A Tale of Two (very different) Secure ICS Architectures
Speaker: Alexandrine TORRENTS, Wavestone
Well, I can’t say this is my favorite talk but I have to start with this presentation as this year was a bit special for me: first time speaker at S4.
I had the opportunity to talk on the Main Stage, right after the keynotes and talk about ICS secure architectures.
No Limits! It gave me the idea of thinking about the future of ICS network architectures.
In this presentation, I compare and contrast the requirements and corresponding secure ICS network architecture of two very different businesses within the same company: power plants and solar/wind farms.
I won’t detail the whole presentation today as I will write a more detailed article in a few weeks just in time for the release of the video on June 13th.
Interview: CISA Director Jen Easterly
Dale Peterson interviewed CISA Director Jen Easterly on the Main Stage.
The video of the interview is already available on S4Events YouTube channel: https://www.youtube.com/watch?v=xOdIUA4lWnI
I found this interview very interesting, and also very inspiring.
Jen presented CISA’s goal: understand, manage and reduce risks, as well as specific objectives for 2022-2023.
One is oriented on processes:
- Baseline goals have been defined to drive common baselines across all sectors.
- Sector specific documents will be added in the next two years.
Another one is oriented on people:
- CISA wishes to expand its ICS team and is recruiting, especially senior ICS experts.
- CISA will create an ICS JCDC workgroup (Joint Cyber Defense Collaborative) to unify defensive actions and drive down risk in advance of cyber incidents related to ICS. The workgroup will include both public and private sectors.
Jen also talked about Shields UP (https://www.cisa.gov/shields-up) . Since Russia’s invasion of Ukraine, intelligence indicates that the Russian Government is exploring options for potential cyberattacks and CISA is asking every organization to be prepared to respond to disruptive cyber incidents. They published several recommendations on their website.
This interview made me think about what could be done within the French cybersecurity agency (ANSSI) regarding ICS cybersecurity. From my understanding, the ICS expertise is spread across different business units. But what if there was a dedicated ICS cybersecurity task force driving all efforts?
Security Truth or Consequences
Speaker: Dale Peterson
Dale presented a Hard Security Truth: Cybersecurity controls at best reduce the likelihood of attack, but they do not eliminate the possibility of compromise.
Indeed, even with the best security controls implemented and the best OT security program,organizations can be defeated by human errors, configuration errors, or 0day vulnerabilities. It is not a game asset owners can win, they can only reduce the chances of losing.
But what if companies could shift to a consequence reduction mindset and maybe win the cyber risk management game?
Let’s take the example of a glass manufacturer. One of the most sensitive PLCs controls the heat of the oven. if this PLC is compromised, it could be very dangerous for the process. Of course, you can reduce the likelihood of this compromise by implementing security controls, such as network filtering for example. But what if the PLC gets compromised anyway? How could you reduce the impact and get back the control of the process as quickly as possible?
Well, do not only think about cybersecurity and focus on the business and its resiliency. Adding a manual control on the production line could do the trick and make sure the consequence of an attack would not be that important.
Well, it is not always that simple but I find it interesting to focus on consequences and find business oriented solutions to reduce cyber risks.
Dale concluded his talk by presenting his 3-step approach for consequence reduction:
- Identify high consequence event within your organization
- Determine if a cyber attack can cause that event
- If yes, find a way that it won’t
This approach looks like a safety approach, but applied to additional consequences not covered by safety, like loss of revenue.
PIPEDREAM & ICS Cyber Threat In 2022
Speaker: Rob Lee, Dragos
Rob Lee was supposed to present his ICS Cyber Treat review but with the recent news, he made a focus on Pipedream, the ICS attack toolkit/malware analyzed by Dragos: https://www.youtube.com/watch?v=H82sbIwFxt4
This toolkit has been developed by the threat group Chernovite and its capability has not been employed yet. Pipedream seems to be the most flexible ICS attack framework to date. It uses ICS-specific protocols for reconnaissance and manipulation of PLCs.
The primary targets of the toolkit include PLCs from Omron and Schneider Electric. However, pipedream capabilities could impact much more PLC vendors.

Rob presented some of these capabilities, as well as potential attack scenarios following the ICS cyber kill chain:
- EVILSCHOLAR – A capability designed to discover, access, manipulate, and disable Schneider Elctric PLCs.
- BADOMEN – A remote shell capability designed to interact with Omron software and PLCs.
- MOUSEHOLE – A scanning tool designed to use OPC UA and FINS protocols to enumerate PLCs and OT networks.
- DUSTYTUNNEL – Custom remote operational implant capability to perform host reconnaissance and command and control.
- LAZYCARGO – Drops and exploits a vulnerable ASRock driver to load an unsigned driver. Works on all Windows systems not just those with ASRock
Dragos published a full report on pipedream: https://www.dragos.com/blog/industry-news/chernovite-pipedream-malware-targeting-industrial-control-systems/
What I find the most interesting in this toolkit is that it does not use a lot of CVEs, but mainly legitimate functionalities of PLCs and industrial protocols to target industrial control systems.
This toolkit was also analyzed by Mandiant, who called it Incontroller. They also made a presentation at S4 and published a detailed report of their analysis: https://www.mandiant.com/resources/incontroller-state-sponsored-ics-tool
Unpwning A Building
Speaker: Peter Panholzer, Limes Security
This presentation was pretty original as cybersecurity experts had to exploit a cybersecurity vulnerability to resolve a cybersecurity incident.
The incident: a building had a complete loss of their building automation system, using KNX devices.
The initial situation: Devices of the building were no longer operational and the vendor recommended replacing the devices (cost > 100k€).
Idea to resolve the incident: the BCU key is a security parameter used to protect the device from being modified; the BCU key was probably set on the device by the attacker. The idea was to retrieve the BCU key and reprogram the devices.
How: the cybersecurity experts asked for some samples of devices, and tried to read the key from the devices. They managed to dump the firmware of one of the devices and access the memory that was not protected. They used a sliding window and with some brute force, they managed to retrieve the key that was written in clear text in the memory.
Resolution: Fortunately (in this case), the key was the same for all devices and it could be used to reset the devices and restart the building automation system

Unprecedented Attack, Unprecedented Response – SUNBURST From The Inside
Speaker: Tim Brown, SolarWinds
You’ve all heard about the SUNBURST cyberattack on SolarWinds in December 2020. In this presentation, Tim Brown, CISO of SolarWinds took us inside and explained how he managed this major incident in the first hours, days, weeks, and months that followed.
Besides the presentation in itself that was very good, the most interesting point for me is about the final thoughts and the fact that this incident has increased the level of transparency expected of vendors.
This event caused many changes and has brought supply chain security even more to the front of cybersecurity discussions.
Using NTIA’s VEX to Tame the Vulnerability Tsunami
Speaker: Eric Byres, aDolus Technology
SBOM (Software Bill of Materials) was kind of trendy this year at S4. Vendors and asset owners should have a SBOM to list all components and libraries used in their products and use it in their vulnerability management process to identify patches to install.
With this, you could end up with thousands of vulnerabilities to patch. But is the vulnerability exploitable in your context?
Indeed, just because a vulnerability database references a particular software component doesn’t mean the vulnerability will actually be exploitable in every software product that includes that component. As a result, organizations can waste valuable time fruitlessly searching for and patching vulnerabilities, even though those vulnerabilities aren’t actually exploitable.
This introduces VEX (Vulnerability Exploitability eXchange), which is a security advisory profile that will be used in combination with SBOM. This profile allows software suppliers to issue a standardized, machine-readable document that states whether or not their products are “affected” by one or more known component vulnerabilities.
You can use VEX for multiple use cases:
- Multiple products to one vulnerability: what products are affected by Log4j?
- Multiple vulnerabilities to a specific product: which vulnerabilities affect the product I use?
The status of a vulnerability includes affected, not affected, fixed, or under investigation.
VEX provides a method for asset owners to focus on exploitable vulnerabilities that present the most risk.
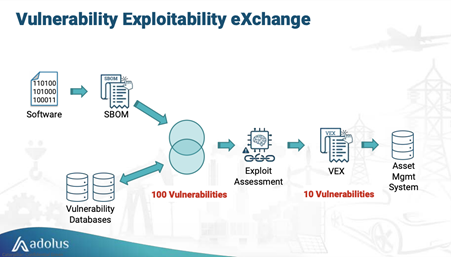
Once you get a comprehensive list of vulnerabilities that could be exploited in your product, as an asset owner, you can use the SSVC methodology to decide what to do in your context with the vulnerability: patch now, patch during the next scheduled maintenance, defer.
Another talk was related to this subject during S4: CSAF, not SBOM, is the Solution, presented by Jens Wiesner from BSI. CSAF (Common Security Advisory Framework) is an open standard about security advisories.

Top 20 PLC Secure Coding Practices
Speakers: Vivek Ponnada, Nozomi Networks and Josh Ruff, Deloitte
The Top 20 PLC Secure Coding Practices is the result of a community effort to provide guidelines to engineers that are creating software (ladder logic, function charts etc.) to help improve the security posture of Industrial Control Systems: https://plc-security.com/
The idea came from a talk at S4x20 where Jake Brodsky asked why engineers and technicians aren’t trained to code and configure PLC’s in a secure manner, and then gave examples of what should be taught and done.
The aim of this session was to present some of the practices in detail and with concrete examples.
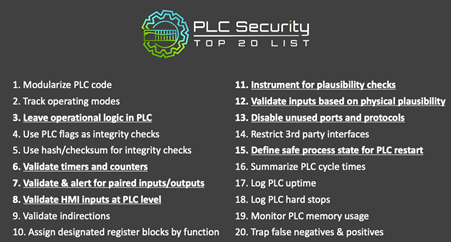
Below are two of the practices that were presented:
- Practice #3: Leave operational logic in PLC
While HMI visualization software provides some level of coding capabilities, this functionality should not be used for control or safety coding
The idea with this practice is to make sure that controls are performed by the PLC itself and not by the HMI. This way, if you bypass the HMI and send a request directly to the PLC, the PLC won’t automatically accept your request but will perform controls to make sure the logic makes sense.
It is similar to the OWASP recommendation in IT to implement controls on the server side and not on the client side for web applications.
- Practice #7: Validate paired inputs/outputs
When mutually exclusive paired inputs or outputs that physically cannot happen at the same time (e.g., motor start/stop, valve open/close) are asserted simultaneously, this may indicate a sensor failure or malicious activity.
The idea with this practice is to implement controls based on inputs/outputs that are linked together. For example, a compressor cannot be started and stopped at the same time. An attacker could turn on both the start and stop outputs simultaneously. To avoid that, a single output could be used to run the compressor with interlocks and delay timers.
If you already know the Top 20 PLC secure coding practices, you won’t learn anything with this presentation but I think it is a great introduction to understand the mindset behind these practices.
Something interesting as well, several talks this year were linked to PLC secure coding practices:
- PLC EDR: Model Checking of Logic
- PLC Library to Detect Abnormalities
You can find out more about these presentations, as well as others in Arnaud SOULLIE’s video on S4: https://www.youtube.com/watch?v=9XCNjmKJiTk
ICS4ICS: Results of the First Major Exercise
Speaker: Megan Samford, Schneider Electric
Like I mentioned earlier, S4 was the stage of the first ICS4ICS exercise on April 18th. ICS4ICS stands for Incident Command System for Industrial Control Systems.
Megan Samford talked at S4x20 about the fact that cyber was the only designated federal disaster type not currently using Incident Command System for its response framework.
Since 2020, a team of more than 1000 volunteers has been put together to create a global framework of cyber responders.
The Incident Command Process is based on a planning P cycle that provides a proven structured process to manage any incident with a standardized approach to organizing and executing work.
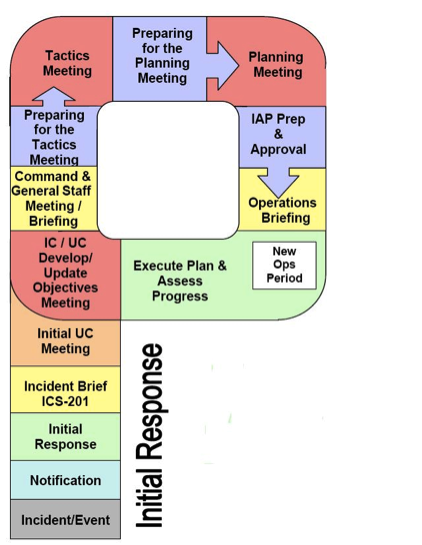
The objective of the exercise was to present this methodology as well as the structure of documents and templates that can be used to follow a cyber incident:
- Cover Sheet
- ICS-202 Incident Objectives
- IICS-203 Organization Assignment List
- ICS-204 Assignment List
- ICS-205A Communications List
- ICS-207 Incident Organization Chart
- ICS-208 Safety Message/Plan
- ICS-214 Activity Log
The goal for ICS4ICS after S4x22 is to expand its capabilities by:
- Conducting ICS4ICS exercices globally
- Offering ICS4ICS credentials and training globally
- Supporting more complex incidents
Of course, ICS4ICS is more of an organizational framework and does not give guidance about the cyber incident itself. I would be interested in the next few years to have insights on how companies actually used this framework and how it helped their ICS cyber incident response.
Finally, if you still have time, I recommend the following presentations as well:
- Cyber Conflict and International Relations
- Assessing the Balance Between Visibility and Confidentiality in ICS Network Traffic
- Inside Industroyer2 and Sandworm’s Latest Cyberattacks Against Ukraine
- The Great Debate: Cyber Insurance Will Play A Major Role In OT Risk Management
- When C-SHTF: Lessons Learned from the Front Lines in OT Incident Response
S4x22 was great! So many good talks but also (and foremostly) the opportunity to see again so many familiar faces of the ICS community and meet new people.
I already look forward to S4x23 that will take place from February 13th to February 16th, 2023. Next year, the conference will still be in Miami South Beach, but at the Loews as the Fillmore will be in renovation.


