Introduction
Cyber Supply Chain attacks are a growing trend amongst cybercriminals where one attack can leave countless organizations vulnerable and potentially damaged. You’ve seen the headlines following a number of high-profile incidents in recent months. The European Union Agency for Cybersecurity (ENISA) warns that these types of attacks are now growing 400% year-over-year as cybercriminals are shifting to larger, cross-border targets.
Attackers’ main motivations remain to gain access to source code and customer data, and now they can do so across multiple target organizations by first compromising vendor software being deployed to those companies and government agencies. This is an ingenious (and nefarious!) approach on a few fronts:
- This type of attack can generally get around any target company’s strong cybersecurity posture, particularly related to its perimeter security; the attack is brought into the target environment via a trusted vendor’s product.
- Such an unsuspected attack vector (a form of “friendly fire”) means that the attacker’s “dwell time” within the target can be quite long before discovered (or revealed in the form of ransomware!). Quite a lot of damage can be done during this time.
- The shear breadth in number of targets that can be addressed via a single attack is immense; the economies for a cybercriminal vastly multiply their criminal profitability.
About 50% of these attacks can be attributed to known advanced persistent threat (APT) organizations (e.g., the Russian state-sponsored threat group APT29, a.k.a. “Cozy Bear”, responsible for the 2020 SolarWinds attack). These APT groups have access to many resources and much funding enabling their creativity for damage and not getting caught. Hence, these attacks are growing rapidly and more complex with such backing; and this trend will continue, enlarging the gap between such risks and an organization’s ability to detect and remediate them in a timely fashion.
Some most notable recent cyber supply chain attacks include:
- SolarWinds – Where attackers in 2020 exploited known vulnerabilities in its IT software Orion (used to manage servers in many organizations, including large businesses, several arms of the U.S. government, threat response firm FireEye, and Microsoft.
- Kayesa – More recently in 2021, the notorious REvil ransomware gang (another APT organization) exploited known vulnerabilities in IT management platform Kayesa VSA, which ultimately compromised an estimated 1,000 organizations that use the platform.
C-SCRM Survival Tip #1: In terms of your organization’s vendors for software or hardware, etc., it turns out that their risk model is now your risk model! Frankly, it always has been, and attackers have evolved to take advantage of this existing threat vector.

Graphic #1: Unavoidably Intertwined Operational Models in Managing Cyber Supply Chain Risk
Hence, the complete Cyber Supply Chain lifecycle for all your business applications and IT tools must be considered within your Cybersecurity strategy and practices. This means that before you choose a vendor, you should assess their security posture and security & incident management processes BEFORE you allow them to contribute software, tools, or equipment to your otherwise secure enterprise.
More so, beyond an initial assessment and acceptance of a vendor’s software, etc., the acceptability of a vendor’s continual access to your environments via releases and patches of their products needs to be continually monitored and assessed.
C-SCRM Survival Tip #2: Shift Security Left. The only way to fully secure your enterprise continually is to ensure the sanctity of anything that comes into it. That includes all vendor products that would integrate into your IT environments, etc., and the vendor’s lifecycle for development and deployment of their products. You can only be as secure as they are!
C-Supply Chain Risk Management – Definition and Scope
Attacks on Cyber Supply Chains continue to take advantage of ongoing disconnects in an organization’s understanding of the related supply chain risks and how to deal with them:
- Most organizations have a false sense of security (“blind spots“) based on assumptions that their vendors are already secure, and their products can be trusted in the organization‘s environment. They believe their recognizable “brand name“ vendors are at least as diligent and proactive about cybersecurity as their organization.
- Many organizations also lack continual robust monitoring and reporting, particularly around their vendors‘ software product interactions within their environments; they’re simply not looking here with sufficient focus based on current events.
- 82% of organizations believe their executive teams and boards are confident in their approach to measuring and managing Supply Chain Risk.
- Yet only 44% regularly report on their supply chain risks and related industry events to senior leadership. This is clearly a blind spot for leadership.
- Looking at financial services firms, for example, 79% say they would decline a business relationship due to a vendor’s cybersecurity performance.
- But lack the data to make such decisions.

Graphic #2: Today’s Growing C-SCRM Threat Definition and Scope
This false sense of security that most organizations have about their vendors’ software, etc. is based upon a (unverified) trust of a vendor’s own security diligence. But we cannot assume this anymore, and perhaps never should have.
This is one big reason driving a growing need for:
- More continual and robust assessment of software (and hardware, firmware, etc.) providers’ cybersecurity performance.
- Improved monitoring and reporting from both: a) upstream software vendors’ environments; as well as b) the downstream software buyers’ environments.
These may seem to be separate issues at first, but they ultimately compound to corrupt downstream customer environments prolifically. Hence, we must “Shift Left” and go upstream into the vendor’s cybersecurity practices in order to manage our own Supply Chain risks.
C-SCRM Survival Tip #3: Both initial and continual assessments of a vendor’s cybersecurity practices and incidents should be analyzed to ensure the security of an organization’s global supply chain before the vendor’s products or services touch their enterprise, and then continually throughout the relationship (and related product updates, patches, etc.).
Another growing need is for the establishment of cybersecurity consortiums of industries and organizations (”IT ecosystems”) to share vendor and product risk data, and to quickly and continually inform partner organizations of new risks and mitigations to ensure fewer downstream surprises. Whether performed per organization or through a consortium information sharing, there is (for the first time) a recognized need for continual assessments of many vendors’ cybersecurity practices before and throughout an organization’s relationship with these providers of solutions within their enterprise. This is an emerging best practice for maintaining your environments’ security.
Because these types of attacks have proven very successful (and profitable) to cybercriminals over the past few years, organizations should expect more and larger cyber supply chain attacks in 2022 and beyond. Hence, the cost of the supply chain status quo is going up and this trend cannot be allowed to persist. This is causing organizations to embrace stronger operational resilience strategies and emerging approaches like never before.
Noted that it is not only financial damage that companies must avoid (or remediate!) in the case of these attacks that often end in data exfiltration and/or ransomware. 83% of compromised organizations have also experienced reputational damage to their brand and public perception of their company. This “ups the ante” for proactive avoidance of such attacks and more work to do if you are attacked.
C-SCRM Survival Tip #4: Supply Chain attacks do more than financial harm to a company; in many cases these may also cause long-term reputational damage! Hence, managing to reduce such attacks but also in robustly handling such attacks is vital to an organization’s survival.
In response to the increasing waves of Cyber Supply Chain attacks, it is no surprise that a global approach to securing their supply chains as well as increasing their operational resilience will be the top priorities for 50% of organizations by 2023. This is survival of the cyber-fittest.
To accomplish this, 88% of companies state that visibility into their global supply chain is more important now than it was 2 years ago. But unfortunately, 74% of organizations are still using inefficient and less adaptable manual methods to ascertain and manage their supply chain risks. Such approaches cannot persist while such risks are increasing at an exponential rate.
For an example of where improved C-SCRM approaches and processes are heading, consider the emerging security ratings services that customer organizations can utilize to initially (and continually) assess the cybersecurity practices and incident management of their vendors. This is another emerging best practice, yet only 22% of organizations are using these resources to continually monitor their vendors’ cybersecurity performance. Expect this utilization to grow and for such services to become more robust with available security tracking data for vendors.
C-SCRM – Current Challenges and Opportunities
The vast number of Cyber Supply Chain attacks are being enabled by many challenges affecting organizations that utilize vendor software. Yes, you are right; this means almost all organizations. Try imagining an organization that does not use vendor software; then pause to think about the many(!) types of vendor software your organization relies on.
C-SCRM Survival Tip #5: Everyone has a cyber supply chain that can be corrupted! There are very few exceptions. In sort, every organization has a cyber supply chain whether the know it or not, complete with risks that can be exploited, and threats brought into their environment unexpectedly … EVEN IF the organization is highly secure in its perimeter defenses.Hence,cyber supply chain risks must be proactively managed by your organization.
It’s quite clear what the breadth of target organizations can be for cybercriminals when they devise such supply chain attacks. They only need to breach a small number of the right vendors to indirectly gain access to their preferred (many!) target organizations amongst a vendors’ customer list.
Some of the current challenges that organizations face in trying to regularly assess their vendor and supply chain cyber risks include:
- Lack of data that is readily available related to such risks, including its timeliness, accuracy, and actionability. Organizations have had to develop their own data for such analysis and decision-making to select or continue with a particular vendor or product.
- This can be (too) time-consuming and resource-intensive for organizations.
- Such data, when possible, is intended to help organizations to identify as early as possible any potential risk exposure when using a particular vendor’s product
- Even when such data is sufficiently available (rarely), most customer organizations have had little sway to force vendors to remediate their internal and supply chain processes to a point that they can regularly be confident in consuming their products as cyber-safe.
- Such data would need to be refreshed frequently to be effective; but even where there are useful data points, these are generally not monitored continuously as would be needed based on today’s changing and escalating threats.
- All this lack of actionable data from the above challenges means that the speed of any assessment is simply too long a cycle.
- Especially true for continual monitoring where the threat is potentially already in your enterprise (vs. an initial assessment before bringing in a product).
- But the only way an organization could previously speed up such assessments was to invest more of its resources into such focused efforts; but it generally didn’t have the capacity to do so.
- Lastly, how an organization would address its 3rd Party risk management is strongly determined by its structure, and defined roles and responsibilities for managing this. Most organizations have not made it clear who (what person or team) would own the responsibility for Cyber Supply Chain Risk Management. This will have to change before many of the challenges above can be addressed considerably.

Graphic #3: Current C-SCRM Challenges and Potential Solutions
There are emerging opportunities and options in addressing the challenges listed above and related ongoing Supply Chain concerns. For example:
- New technologies are becoming available to organizations that wish to be more proactive and quickly adaptive to their supply chain risks.
- 3rd Party Security Ratings – Services are becoming available where an organization can purchase one-time or recurring ratings for a particular vendor or set of products it wants to purchase (or already has).
- Advanced Monitoring and Detection Tools and Services – Continued advancement and maturity of monitoring, detection, and action-oriented tools and services is enabling earlier detection and appropriate actions than ever before.
- AI and its behavior analysis capabilities – This is one important advancement amongst monitoring and detection tool improvements; but this technology is also becoming engrained within many other aspects of cybersecurity
- Wherever unusual patterns can be recognized by AI and enacted on appropriately far more quickly than a human could.
- Expect AI to become a primary underpinning to many cybersecurity automation tools, not just C-SCRM.
- For supply chains, Blockchain is an emerging technology that will enable better security management in terms of a product manifest’s chain of custody and that it has not been tampered with during the supply chain deployment.
- Note, however, that this doesn’t solve the issue of a vendor’s software development process being breached to inject a threat for downstream users; this risk would need to be assessed as part of the vendor’s security practices (see the 3rd Party Security Ratings services above).
- Perhaps most importantly, new organizational roles (and responsibilities) are being created to enable greater focus and proactivity in assessing and managing supply chain and other 3rd Party risks. This is long overdue, and a promising development in appropriately applying all the risk mitigation options listed above as needed for a particular organization’s target security posture.
If Every Organization has a Cyber Supply Chain that Can Be Corrupted to Create Extensive Damage à What are you going to do about it?
Every organization has a supply chain with risks that can absolutely be exploited; there are no meaningful exceptions to this rule. Hence, there is no room for a false sense of security, and no excuse to not address this immediately (and ongoing). After all, you do not want to be the next cautionary tale about an organization in industry news!
To get started with your organization’s C-SCRM strategy, first consider these Success Factors in developing your overall approach. Remember these factors as the “B-O-O-M“ strategy to pursue when ensuring C-SCRM success:
- Both internal and external supply chain processes and security checks require focus.
- There are clearly a number of processes and capabilities that an organization has direct influence on immediately; start there, but do not end there.
- Be sure to also include external forces, such as suppliers, where the organization has only indirect influence; but where failure to implement such influence creates greater risk.
- Manage all threat vectors associated with your cyber supply chain risks; hence manage your supply chain vendors as well as your own organization.
- Optimize Your Organization and related processes to stay aware of current cyber events, industry trends, issues, and best practices.
- Ensure sufficient focus by your organization on these items, including assigned roles and responsibilities for coverage.
- Partner with industry organizations and vendor partner organizations to stay informed and influential for managing supply chain risks.
- Optimize Your Data for cyber supply chain and vendor risks, and extensively analyze these to be data-driven in your C-SCRM capabilities prioritization as well as your vendor selections and ongoing risk management.
- Mature your organization, data, and tailored best practices to keep pace with (or preferably ahead of!) the continually growing and evolving cyber supply chain threats you must manage. This is far from a static set of threat vectors in this cybersecurity space and may just be in its infancy in terms of the future number of threats and types of complexity to be managed!
Graphic 4: Success Factors for Managing Cyber Supply Chain Risk
C-SCRM Survival Tip #6: Drop the “BOOM” to be successful in your C-SCRM strategy and approach: Both internal and external forces need to be managed; Optimize your organization for C-SCRM coverage; Optimize your C-SCRM data for analysis, selection, and monitoring risks; and Mature the above as organizational-specific best practices to stay ahead of the curve!
Defining & Implementing C-SCRM Best Practices for Your Organization
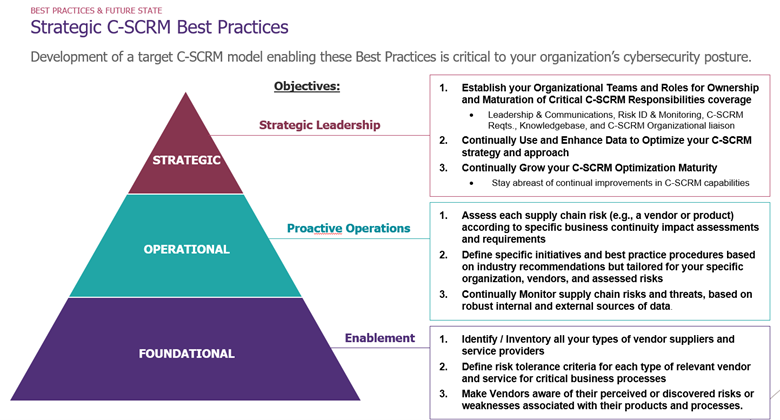
The previously listed success factors for C-SCRM lead directly to the following best practices and capabilities for an organization to implement (shown here in a step-wise approach):
- Identify / Inventory all your types of vendor suppliers and service providers.
- Define risk tolerance criteria for each type of relevant vendor and service for critical business processes.
- Including important vendor dependencies, their critical software dependencies and single points of failure, etc.)
- Assess each supply chain risk (e.g., a vendor or product) according to their specific business continuity impact assessment and requirements.
- Define initiatives and best practice procedures based on industry best practices tailored for your organization and assessed risks.
- Establish your organizational teams and roles for ownership and maturing these critical C-SCRM responsibilities, including –
- C-SCRM Leadership and Communications – Report to Executive Team & Board regularly about risks and threats to the organization and identified in the industry (that may become threats which can be proactively avoided).
- Risk Identification and Monitoring – Continually assess prospective and current vendors via software and service types with their risk profiles and requirements.
- Cyber Supply Chain Requirements – Actively manage each vendor’s adherence to the organization’s C-SCRM established requirements; and hence, their incorporation into vendor contracts.
- Cybersecurity Knowledgebase / Data Repository – This resource should be maintained to be more broadly used than just for C-SCRM scenarios; but this is where business line managers as well as technical integrators can access requirements lists, contractual provisions, and ratings data associated with vendors and their products.
- Supply Chain Risk Liaison to the rest of the organization – In the case of insufficient data available for a vendor-related cybersecurity decision, or the needed investigation into a new vendor, product, or incident.
- Continually monitor supply chain risks and threats, based on internal and external sources of data.
- Including findings from suppliers’ performance monitoring and reviews.
- Maintain historical and trend data as long as relevant.
- Make vendors aware of perceived or discovered risks or weaknesses associated with their products and processes.
- g., managing such vendors throughput their entire product lifecycle, including procedures to manage releases, patches, and end-of-life considerations.
- In some cases, you can help them improve their cybersecurity capabilities to advance your own security posture.
- But if they fail to adhere to your supply chain security requirements or attempt to remediate based on findings you share, all bets are off.
- Continually use and enhance data to optimize your C-SCRM strategy and approach.
- Strive for C-SCRM process and data maturity in both selecting vendors as well as strengthening these relationships (and your trust in them) over time.
- Also use data to build an appropriate operational resilience strategy that will take over in the case of a vendor’s failure – via an attack needing remediation and/or the subsequent removal of such a unacceptable vendor or product.
- Grow your C-SCRM Optimization maturity.
- This will never be a static set of vulnerabilities or threat vectors; stay diligent at continual improvement and maturity in your organization’s capabilities to actively avoid supply chain risk and to remediate it quickly if encountered.
The listing above of C-SCRM best practices was laid out in a suggested chronological order (do this first, second, and so on). However, for further elaboration on implementing your best practices, the list below in Graphic #5 shows these same best practices in relation to achieving organizational C-SCRM strategic objectives.
Graphic 5: C-SCRM Best Practices to Implement Now and Ongoing
C-SCRM Survival Tip #7: Implement your C-SCRM Best Practices in the order that makes most sense for your organization’s transformation into C-SCRM maturity; but ensure these accomplish the strategic objectives above as you mature.
Conclusion & Next Steps
So, to what extent do you need a C-SCRM strategy? By now you should understand the value for any organization to have such a strategy and accompanying best practices. But the extent to which SCRM should be aligned with and support your business and IT strategies will depend on your business model, vendors profile, cybersecurity capabilities, and risk tolerance.
How important are your vendors’ products (e.g., software, tools, hardware, or firmware) to your critical business operations? Or to your potential growth? How fragile are your business operations if a vendor in your supply chain was no longer a secure option? What is your feasible risk tolerance for such external disruptions to operations? Think about these questions regarding your supply chain, vendor and product choices, and ongoing operational resilience requirements to determine how to develop your specific C-SCRM strategy for current and future needs.
Once you’ve determined the next steps that are appropriate for your organization, here are a few ways that Wavestone can assist you when you’re ready to build out your Cyber Supply Chain Risk Management optimization approach to enhance, baseline, or continually improve your C-SCRM capabilities:
- Develop a customized C-SCRM strategy for your organization.
- Establish a Cyber Supply Chain Center of Excellence (CSC-CoE) with robust C-SCRM capabilities for vendor-related decision-making as well ongoing monitoring and reporting at all organizational levels.
- Execute a C-SCRM (Vendor & Product) Capabilities Maturity & Risk Management Assessment to identify any vulnerabilities, risks, or threats; as well as to enable targeted decision-making about selected vendors or products of interest.
Feel free to reach out to us if you’d like to discuss your Cybersecurity journey and capabilities, and how to get started towards supply chain risk management success.
About Wavestone US
Wavestone US is the North American arm of global management and IT consulting firm Wavestone. We have supported the transformations of more than 200 Fortune 1000 companies across a wide range of industries, leveraging a strong peer-to-peer culture, offering a practitioner’s perspective on IT strategy, cost optimization, operational improvements, cybersecurity, and business management. It is our mission to help business and IT leaders successfully deliver their most critical transformations and achieve positive outcomes. We drive change for growth, lower cost, and risk, and create the trust that gives people the desire to act.


