Active Directory (AD) is a directory provided by Microsoft since Windows 2000 Server, that centralises the mechanisms for identifying, authenticating, and managing access rights to the organisation’s resources. This component is adopted by a significant number of organisations (approximately 90 to 95 percent of companies with more than 1,000 employees use Active Directory [1] [2]), making it a real market standard.
In recent years, AD has been frequently targeted by attackers, as it has been compromised in 100% of the cyber-attacks managed by CERT-Wavestone, with the intention of using the access gained to spread malware (e.g., ransomware) throughout the IS or to access and leak a large amount of sensitive information from an organisation.
However, its degree of security remains highly inadequate: In 2018, 96% of penetration tests carried out by Wavestone on 25 information systems of prominent companies resulted in total compromise. Even though this value has been decreasing over the past two years, it is still close to 90%.
As this has become an absolute priority for most organisations, corporate cybersecurity teams have launched major programmes to strengthen the AD’s security level. Organisations are searching for solutions to help them in addressing this complex, wide-ranging project, that includes top priority topics such as the implementation of tiering.
By analysing the market, we have identified 4 use cases on which these tools are positioned:
- Analysis and audit
- Hardening and maintenance in security condition
- Detection
- Response and Rebuild
The following radar shows a set of vendors providing solutions for these four use cases related to Active Directory security.
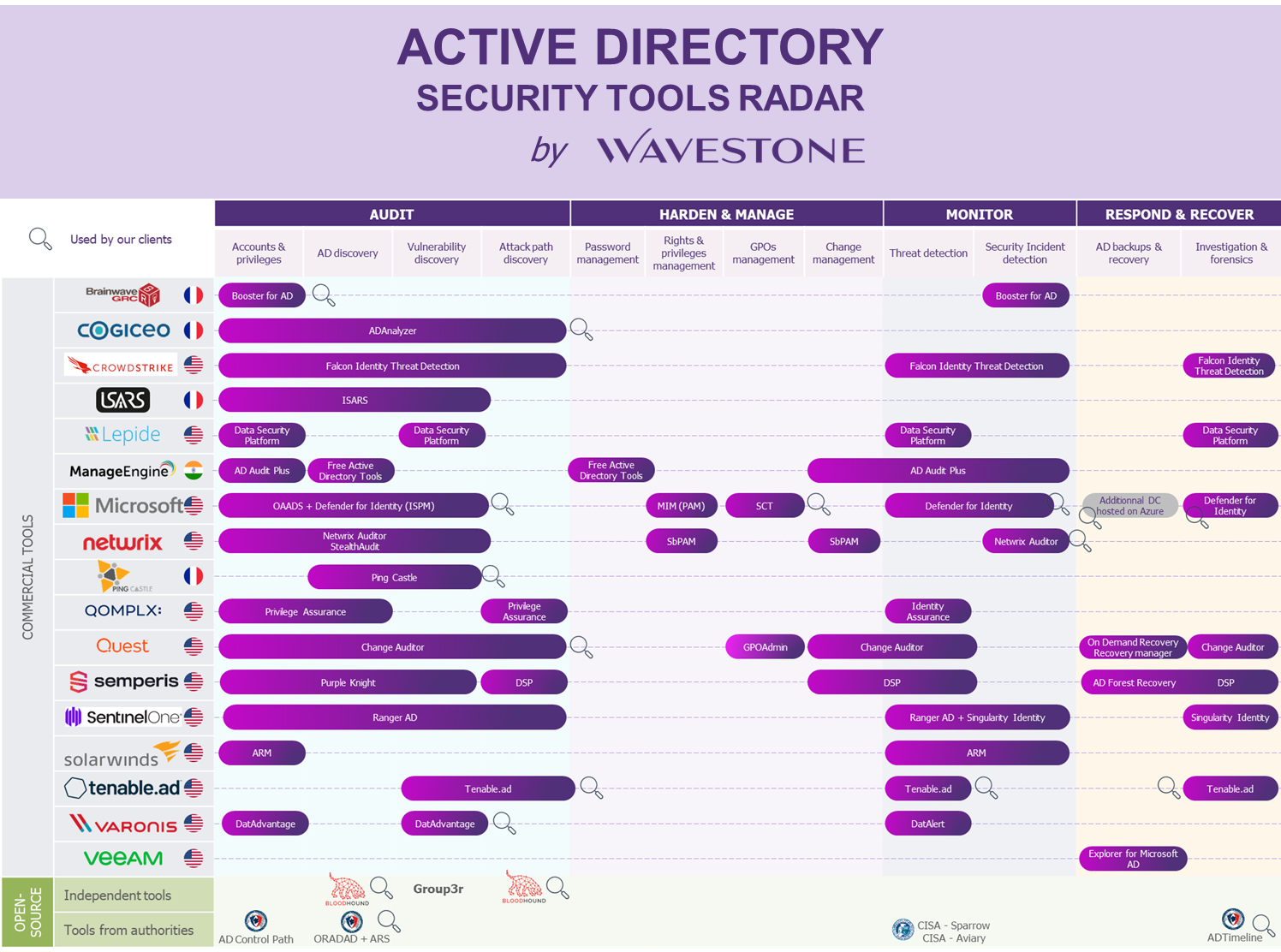
Last update : April 2023
SPECIALISED TOOLS, EACH ANSWERING A PART OF THE EQUATION
“AUDIT”: MAP THE AD AND IDENTIFY ITS VULNERABILITIES TO STRUCTURE AN ACTION PLAN

Before starting any action to improve security, it is necessary to identify the starting point, by establishing an initial inventory. To do so, you can use an audit tool to examine various aspects of the AD configuration, such as obsolete protocols, obsolete OS versions, out-of-date functional levels, password policies, approval relationships with other AD forests, privileged accounts, and the granting of rights that could lead to compromise paths, among other things.
These tools are traditionally used by offensive security teams (internal or external), but we are increasingly observing a recurrent use of this tool by teams in charge of Active Directory MCO and security teams throughout the project to track the rectification of identified vulnerabilities month after month.
For the identification of AD vulnerabilities, tools such as PingCastle (open source), Purple Knight (Semperis), Group3r (open source) ADAnlyzer (Cogiceo) and OAADS (Microsoft) can be used. For compromise paths, BloodHound (open source) or AD Control Path (open source, ANSSI) can be used.
Finally, for regulated and public-sector operators in France, ANSSI offers the Active Directory Security (ADS) service [3], which enables critical operators in assessing their security level.
It should be noted that all audit solutions produce security reports on various reviewed elements, sometimes with a maturity score (that may be based on the Active Directory checkpoints provided by the ANSSI [4]) and technical indications for the correction to be made. The cybersecurity teams should then analyse and put various vulnerabilities in the light of the company’s context (e.g., priority areas, links with other ongoing projects, a more global security trajectory, etc.), create an action plan by first identifying the impacts associated with their implementation, prioritise the deployment of corrective actions, and ensure that they are effective.
“HARDEN & MANAGE”: STRENGTHENING THE SECURITY LEVEL OF THE AD BY APPLYING GOOD PRACTICES

It is not easy to keep Active Directory secure on a daily basis. Every day, changes are made at various levels (e.g., creating accounts, adding accounts to groups, granting rights to accounts, modifying GPOs, changing security policies, etc.), which can, in some cases, expose the Active Directory more than one can imagine.
Firstly, detecting vulnerabilities without delay and without taking manual actions might be an accelerator if adequate governance is in place to deal with the alarms raised. To this end, products such as Tenable.ad (Tenable), Directory Services Protector (Semperis), and Security Compliance Toolkit (Microsoft) can provide real-time visibility of vulnerabilities, allowing for increased reactivity in remediation. It should be noted that some organisations prefer to use auditing tools on a regular basis (i.e., many times a month) to identify and address the delta.
In addition, a range of tools exist to improve overall visibility, simplify day-to-day management, and thus enhance security, or to identify configuration changes that have been made. For example, AD Audit Plus (Manage Engine) or DatAdvantage for Directory Services (Varonis) allows you to receive all the details concerning a change and be notified, if necessary, while Booster for Active Directory (Brainwave) or Privilege Assurance (QOMPLEX) boosts the overall visibility of the AD. Furthermore, Quest’s suite of tools, ActiveRoles For Server to complete delegation management, Change Auditor to identify configuration changes, and GPOAdmin to maintain control of GPOs can complement the tools available to the AD MCO team.
Finally, in terms of improving privileged account management, we can refer to Stealthbits Privileged Activity Manager (Netwrix), which incorporates a PAM solution that makes possible, for example, just-in-time administration (granting privileges to an account only for an operation to be carried out and not permanently).
“MONITOR”: DETECT COMPROMISE ATTEMPTS BEFORE THEY SUCCEED

With the security configurations now enabled, Active Directory is more difficult to compromise, but it is not immune. It is therefore essential to continuously monitor it, in order to be able to detect the first signs of an attack.
In addition to the detection scenarios implemented in the SIEM by the SOC teams, based on the correlation of previously collected logs, specialised tools can complete the system. The latter retrieve data directly from the Domain Controllers either through an agent or an account, and then perform their own correlation and detection processes.
In this category of tools, we can cite Tenable.ad (Tenable), Directory Services Protector (Semperis), Falcon Identity Threat Detection (CrowdStrike), Ranger AD & Singularity Identity (SentinelOne) or DatAlert (Varonis).
“RESPOND & RECOVER”: INVESTIGATE COMPROMISES AND REBUILD THE ACTIVE DIRECTORY

In the event of a partial or total compromise of the AD, two actions should be carried out quickly and in parallel
– Forensics, to understand how the attacker proceeded and what level of confidence one can have in the AD in its current state.
– Restoration / reconstruction of the AD, depending on the case.
To carry out the necessary investigations and attempt to trace the source of the initial compromise, we can suggest the ADTimeline tool (open source, ANSSI), that allows to trace the modifications made to an AD via replication data.
Completely rebuilding an AD environment can take several days or even weeks, which can have a major impact on the organisation. Minimising this time can be vital in some cases. Some tools that can help reduce this time include Active Directory Forest Recovery (Semperis), which automates the Microsoft Forest recovery process, and Recovery Manager for Active Directory (Veeam), which combines compromise-proof backup and recovery when needed.
It should be noted that some organisations choose to outsource (after encryption) the backup as well as to automate and regularly practice the reconstruction, or even to host one of the forest’s Domain Controllers on a third-party platform to maximise the chances of successful restoration, by diversifying the means of backup.
WHAT ABOUT AZURE AD?
Given that many companies are now in a hybrid mode, it is advisable to integrate Azure AD into the scope of the security project as soon as possible. Some tools that can be mentioned within this context are:
– On the “Audit” section: Microsoft 365 DSC, BloudHound (now including an Azure AD part)
– On the “Harden & Manage” section: CoreView, Idecsi, Microsoft tools (Azure AD Access Reviews, Azure AD Entitlement Management, Azure AD Privileged Identity management, etc.)
– On the “Monitor” section: Azure AD Identity Protection, Microsoft 365 DSC
– On the “Respond & Recover” section: Azure AD Identity Protection, Quest On Demand Recovery
IMPORTANT POINTS ABOUT USING TOOLS
Deploying a tool alone does not increase the security level of AD environments. Once a tool has been acquired, it is important not to neglect the rest: defining and implementing governance (processes, organisational model, comitology, steering, reporting, control, continuous improvement, etc.) and the resources with the right expertise to make security improvements effective (dealing with alerts, correcting vulnerabilities, carrying out continuous improvement actions, etc.).
Also, a series of related projects to be carried out and processes to be reviewed during AD security projects, should not be underestimated: patch management, inventory, rationalisation (limiting the number of domains/forests in order to make it easier to maintain them in a secure condition), review of the backup strategy, reconstruction training, construction of restoration/clean-up infrastructure, etc.
Finally, when deploying these tools, keep in mind not to further expose the Active Directory: installing agents on Domain Controllers, opening network flows, granting privileges to accounts or service accounts, etc.
ABOUT OUR METHOD
The radar was built on the basis of a survey of tools on the market. On this basis and in relation to the recurring themes of Active Directory security, a categorisation has been established to facilitate reading.
The tools presented do not claim to be exhaustive, as the number of tools that can contribute to Active Directory security in any way is extensive. This radar is thus a review of the prominent existing tools, notably those encountered frequently by Wavestone consultants in organisations (considered, studied, tested and even deployed).
[2] https://www.silicon.fr/avis-expert/repenser-la-securite-dactive-directory-a-lere-du-cloud


