DECRYPTION
The marketplaces of stolen data


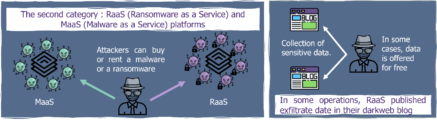
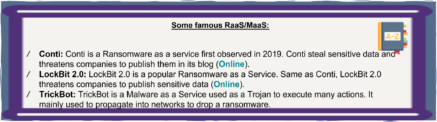

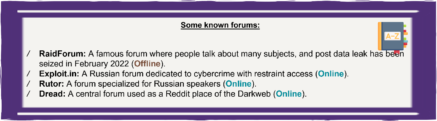

Which type of data are sold?
The different platforms of marketplaces sell different types of data. While some platforms are really focused on selling one specific “product” (eg. hacking forums where Initial Access to companies is sold, as well as auction sites to sell stolen data eg. REvil and its auction site back in 2020), other platforms thrive with a very wide panel of goods, ranging from various weapons to “fullz” (full data about people: Social Security numbers, Bank account numbers, ID,…) without forgetting per-install malware service and financial information about a company. Overall, personal data is one of the most common types one can find on these marketplaces, as well as organization initial access, and non-financial or financial accounts/credentials.
When it comes to prices, whereas the number and variety of data items sold are increasing, the prices are declining as the market grows.
The price of an Initial Access depends on its quality, but it ranges from a couple of hundred USD for a small company to hundreds of thousands of dollars for the bigger ones. The average price is $7,100 in 2021. Patricia Ruffio listed here the prices found per type of data, from credit card data with account balance up to 5K ($120) to social media account ($65 for a gmail account), going through PayPal account logins ($150 for 50 accounts) and European Passport ($3,800). In comparison, DDOSing an unprotected website for a month now costs $850 on average and installing malware on a thousand devices ranges from $45 to $5500 depending on its quality and success rate.
Last but not least, some ransomware groups such as BlackByte go as far as selling stolen data on dedicated auction sites, not only as a means of pressure on victim companies, but also as a very juicy second revenue stream, with starting bids reaching up to $500,000.
What’s the selling process?
Besides a classical strategy of competitivity between the different marketplaces, based on discounts or fidelity points, the platforms are fighting over a security aspect in order to gain the buyer’s trust.
With the growth of marketplaces comes a strong trend for the sellers to strengthen their client’s trust. Taking advantage of legal uncertainty, these websites or events like the Evolution Marketplace exit scam with over $12 million in Bitcoin have greatly tarnished their reputation and taken its toll on customer and vendor trust.
As a result, along with the numerous DDOS protection, layers marketplaces now hide behind to prevent attacks from rivals, the quality of vendors and their items is now more thoroughly assessed and monitored. Direct scams are supposedly prevented by using the marketplace platform as an intermediate deposit for payment so that a client may be refunded in case of deception by the vendor. All transactions are currently mainly in Bitcoin and Monero for anonymity purposes. Some auction and IAB platforms even sometimes use mandatory referral systems to shield themselves from outsiders & untrustworthy members.
Consequently, dark web marketplaces seem more reliable and stolen data is more prone to be sold quickly.
Once sold, what are the stolen data used for?
The financial reason is undoubtedly the main aspect for many actors in the market: most of these data can be used directly for blackmail of course, or to launch another cyberattack with a bigger impact…and more gains. It can be “standard” attacks such as personal data simply used as a basis for phishing operations and for compromising, for example, bank accounts, or it can be larger attacks. In fact, the average ransom paid by companies rose up to $541k according to the 2022 Unit 42 Ransomware Threat Report, highlighting the high profitability of simple ransom and blackmail with the stolen data. While not as straightforward, leveraging stolen Social Security Numbers, IDs, Credit cards are other ways to generate profit or to gain access to companies using identity theft.
However, stolen data may be used for more varied purposes. Corporate espionage is one of them: should a competitor be informed of a potential data leak, and what prevents it from looking at your deepest hidden secrets? It can also be a political matter: for example when Lockbit2.0 hits the French ministry of Justice, the main concerns shift to who laid their hands on such potentially sensitive pieces of information and what their intentions are. Another example of societal impact would be the data breach of Pfizer/BioNTech vaccines data in 2020, which led to attackers modifying the stolen data on the vaccine and publishing them with the headline “Vaccines are malicious”.
What are the impacts on my organization?
As mentioned, the collected data such as initial access can be the essential vector to compromise an organization’s SI and lead to even more impacting attacks. Besides, the main victim’s perimeter is not the only one compromised: the whole ecosystem of partners, clients, and providers… can be affected. If the ransomware is the first type of attack coming to mind after a data breach, one should not underestimate the impacts of identity impersonation and fraud, targeted DDoS…
As it has often been proven and discussed these last years, the financial impact of such compromission can be colossal and even led organizations to their end. Besides, the cost of the attack itself is not the only one to be taken into account. Other components must be considered: loss of customer’s trust, loss due to potential system’s unavailability, cost of intervention from experts to investigate, but also cost of new customer acquisition to win back those that have been lost. Just as an example, Equifax announced that the data breach it faced in 2017 cost around $1.5 billion dollars if not more.
The financial and reputational impacts are intrinsically linked. Indeed, upon facing a data breach, a company is very likely to get customer or partner disengagement. According to a report from IBM, the lost business contributes to 38% of data breach costs. Companies also handle PII (Personally Identifiable Information) which, if stolen, can lead to additional legal costs, class-action settlements, or fines from public institutions.
The total cost of a data breach could be deadly for some companies and must be acknowledged. Equifax spent several million in fines and settlements after dealing with its massive data breach in 2017.
Last but not least, the social and political aspects must not be neglected. Last year, the Labour Party suffered a data breach through a ransomware attack on a third-party supplier. This kind of attack can lead to disinformation campaigns or even interferences in the election process.
In order to prevent a data breach, beyond cybersecurity basic actions, companies must enhance their maturity level when it comes to data security. Evaluating the value of the data is one of the key: the more attractive the data is, the greater chance an attacker will try to steal it. Storage and network security, Identity and Access Management, Cyber Resilience are some of the topics to be addressed at first. On top of this, companies should also focus on creating a strong watch on cybersecurity events and implement, even small, Cyber Threat Intelligence programs. Looking at the cybercrime ecosystem as well as spotting potential attack vectors and modus operandi is never a bad idea to anticipate a cyberattack.
CERT-W: FROM THE FRONT LINE
The First Responder Word

Reading Of The Month
We recommend the Citalid overview of the
Russio-Ukrainien conflit’s cyber aspect
(click on the picture)
SEE YOU NEXT MONTH!!




