Confidential and strategic, the due diligence phase that precedes an acquisition regularly takes place behind closed doors. This phase aims to analyse the target company for an acquisition, in order to determine its level of maturity and compliance on various aspects (strategic, legal, financial, accounting, etc.) and confirm the relevance of the operation.
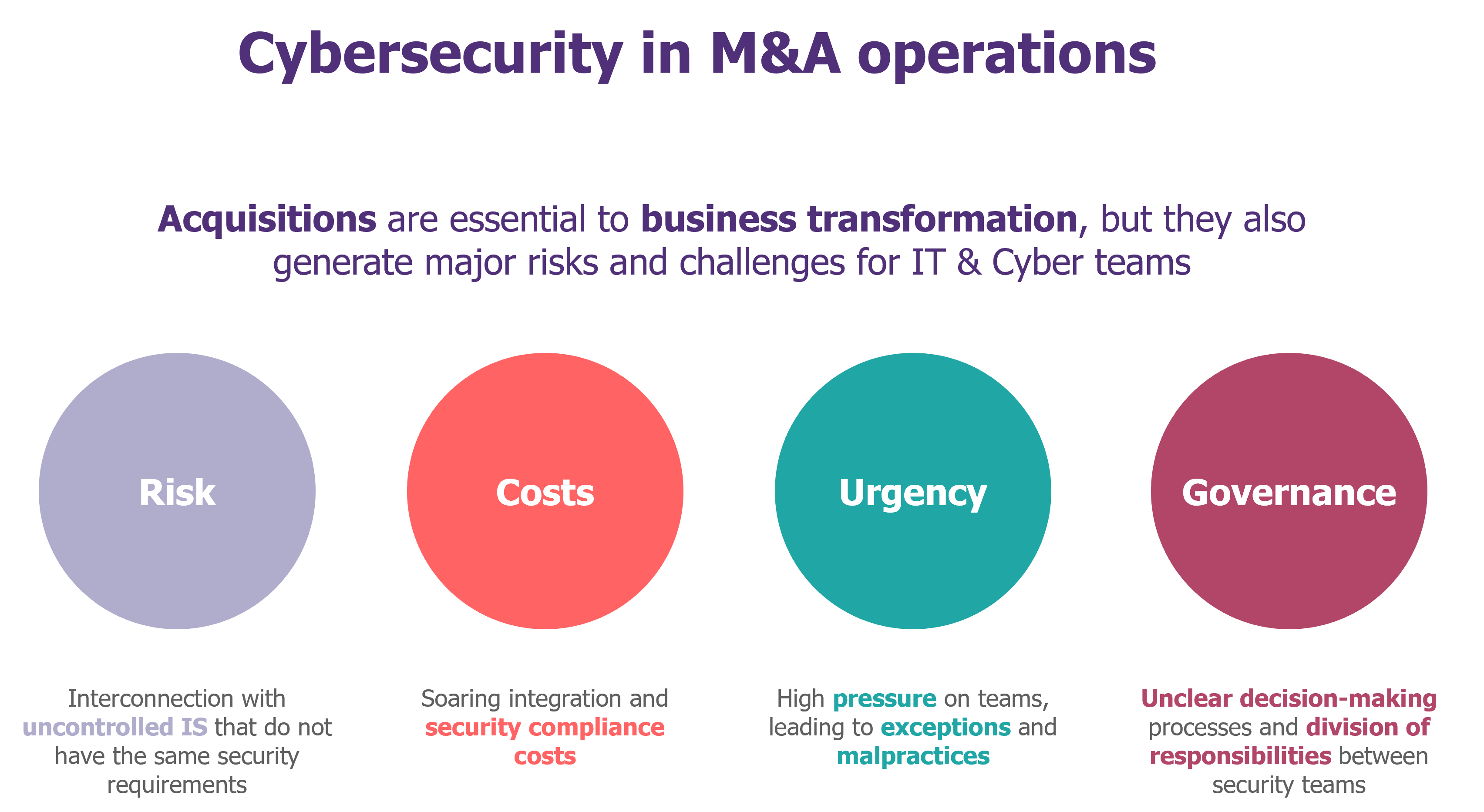
Acquisitions are an ideal time for attackers. With heterogeneous levels of security or uncontrolled interconnections, it becomes possible to attack the acquiring company by rebound, using the acquired company as a gateway.
To manage these risks, cybersecurity must be a key factor in the success of acquisitions and mergers, from the due diligence phase onwards.
Variable cyber needs
Cyber due diligence can bring significant value to cyber, IT and business teams. The results can be used to support decision-making at several levels.
- Understanding the level of maturity of the target company: analysing security practices and identifying gaps in relation to the acquirer’s standards in order to understand the cyber risks incurred during the integration of the new IS.
- Test the level of security of a solution (mainly IT or Cyber): ensure security and resilience to confirm the value assessment (compliance with secure development practices, absence of critical vulnerabilities, preventive security measures, etc.).
- Estimate the cost of the integration: assess the cost of upgrading on the basis of the security debt and the charts to check the relevance of the operation and negotiate the acquisition price which absorbs the integration costs as far as possible.
- Assess reputational risks: ensure compliance with regulations, particularly on personal data, and the absence of intrusions that could damage the reputation of the acquirer after the transfer of ownership.
Cyber due diligence remains nonetheless a special exercise. The company under review (target) does not yet belong to the acquiring company, and the constraints imposed by the teams in charge of the operation or by business teams can be tough.
A business context to take into account when choosing the cyber due diligence method
On the acquirer’s side:
- The budget: the choice of method is correlated to the availability of cyber security teams or a dedicated budget for calling in an external service. It is preferable to secure a contingency with the M&A teams before any operation, to leave yourself a margin of choice.
- Time: business or competitive constraints can have an impact on the due diligence period. The choice of method depends fundamentally on the time given to the cyber teams to conduct their investigation.
On the identified company side:
- Size: the due diligence method must be consistent with the size of the target company’s information system, the nature of its assets and the types of technology used.
- The “balance of power”: the difference in weight between the acquirer and the target company has a major influence on the possibility of conducting an in-depth and transparent cyber analysis (ability to obtain information, evidence, interviews, tests, etc.).
- The core business: the valuation must focus on what makes the identified company valuable, particularly when it comes to an IT product or know-how.
Based on these criteria, as well as existing processes, the cyber and M&A teams work together to choose the method best suited to their needs and the situation.
Cyber due diligence for every operation
Non-intrusive methods
The cybersecurity team may opt for non-intrusive due diligence methods when they have limited resources or when the target company is coveted by other potential acquirers.
1) The security essentials questionnaire is used to measure the pre-identified company’s maturity in terms of the key areas. It has the advantage of being easy to deploy, without imposing a major burden on either the target company or the acquirer.
- Our conviction: it is particularly well suited to assessing the cyber maturity of small companies (fewer than 50 employees). This questionnaire is to be defined by the cyber security teams in collaboration with the IT and M&A teams.
2) “Automatic” cyber-scoring tools can be used to measure the level of security of assets exposed on the Internet. They have the advantage of providing security teams with an immediate view. Beware, however, that their results can be simplistic, as these tools only focus on the tip of the iceberg (what about partner management, cloud security, etc.).
- Our conviction: we do not recommend prioritising their use in a cyber due diligence context, but they do have the advantage of providing a wealth of additional information quickly if your company has already subscribed to an offer.
In-depth methods
The cybersecurity team can opt for more in-depth due diligence methods when they have the human or financial resources and a “favourable balance of power” in the negotiation of the operation.
1) The Due Diligence questionnaire, based on the acquirer’s internal cyber standards, is used to measure the target company’s level of maturity and to identify any deviations from its own policies and standards, an essential prerequisite for quantifying the potential cyber integration costs.
- Our conviction: this is the most widely used method on the market, and enables us to prepare for the integration (integration scenario, cost scenario, planning, etc.). This questionnaire is to be defined by the cyber security teams in collaboration with the IT and M&A teams.
2) Cyber assessment platforms (such as Cybervadis, Risk Ledger, CyberGRX…) can be used to assess the target company’s level of maturity in relation to benchmark security standards, and sometimes even to obtain upgrade action plans.
- Our conviction: the use of platforms is worthwhile if the target company is already registered/assessed. This also allows to pool resources with your “third party” approach (see RiskInsight article on third party management here). Otherwise, it often takes too long.
3) The technical audit provides an in-depth measurement of the level of exposure of a company or asset. Although penetration testing remains the most comprehensive audit, there are other types of tests that are easier to implement in a due diligence context (AD configuration scan, architecture audit, EDR report, report on penetration tests already carried out, etc.).
- Our conviction: it is generally impossible to carry out tests before closing (the assets have not yet been purchased). In the absence of comprehensive tests, the free version of PingCastle provides a simple, accurate and rapid overview of the security level of Active Directories.
While Cyber Due Diligence is a necessary pre-requisite for all M&A operations, it should serve as a leitmotiv for bringing together cybersecurity, M&A, and IT teams to best guide companies in their transformation.
Finally, there are situations in which Cyber Due Diligence could not be carried out (confidentiality, tight schedule, competitive pressure at the time of the operation, etc.). Cyber Due Diligence is often transformed into a 360° audit carried out post-signing/closing. This audit has a new objective: to help define the integration strategy.
–
We’d like to thank Arielle Attias for her contribution to the writing of this article.


