Active Directory is a critical asset whose failure affects a large portion of your information system
Your company is currently dealing with a major ransomware crisis. Given its central role in managing access, authentication, and network resources within any organisation, cybercriminals have compromised the Active Directory in 100% of these crises.
Your systems are now encrypted if the attackers have activated the malicious payload. They might otherwise be isolated and unavailable. In either case, your company no longer has the necessary resources to function properly, and your activity has either ceased or has been significantly slowed!
In this case, trust in your information system has been broken. Your teams begin to feel business pressure, and one question persists: when will we be able to reopen our services? Your goal then becomes clear: you must restore Active Directory with a high enough level of trust to reopen services as soon as possible.
Rebuilding an Active Directory is a difficult step in crisis management. If poorly executed, your organisation exposes itself to two major risks: exacerbating the operational impacts for the business or introducing a new threat to your environment.
The ANSSI has recently published three very comprehensive guides on this subject [1], which we recommend you read.
In this article, we will go over some of the items that stood out to us during crisis management. Our teams were able to overcome numerous obstacles during their interventions. What are the main issues that have arisen? How can they be fixed?
From compromise to reopening: advice to overcome obstacles
Start remediation efficiently with a proven organization
Time lost due to poor crisis organisation can exacerbate the consequences of an Active Directory compromise. Teams are frequently unsure of what to do, who to involve, and what goals to pursue. A delayed response will increase remediation costs, revenue losses, and have an impact on the company’s reputation.
Before the crisis…
It is necessary to identify all the key players to involve in the reconstruction of the Active Directory:
The executive committee will resolve fundamental issues. For example, do we prioritise reopening critical services quickly for business reasons or slowly and securely? There are several possible postures, each with advantages and disadvantages [1 – Strategic Dimension]. The entire remediation plan is based on this decision, so the executive committee must make a decision to begin work immediately.
Business teams will identify and prioritise the most critical services for restoration. The Active Directory compromise affects the majority of the company’s services, and your teams will be unable to handle all requests at once.
Intervention teams (technical and security) will be formed to define and implement the remediation strategy. Because of the expertise and human efforts required to rebuild an Active Directory, temporary reinforcement of your teams is required to handle the remediation: mastering configuration review tools (PingCastle, Purple Knight, etc.), prioritising detected vulnerabilities, deployment and control of measures, and so on.
It is critical to define processes and reflex cards in order to optimise each actor’s reaction time. Simulations and regular exercises should be organised in addition to their writing to train your teams to react effectively.
During the crisis…
Rapidly implement a project monitoring system that includes regular reports, action tracking, and coordination among the various teams involved. Too often, a lack of communication and information leads to a slowdown in remediation. It is not uncommon for administrators to take initiatives without taking the time to communicate them, such as opening more network ports than necessary, parallelizing two tasks from the remediation plan, and so on. These well-intended initiatives can have a significant impact on remediation, ranging from complicating the work to a distorted view of the true security level following the security work, and thus an increased risk of new lightning compromise.
Ensure the resilience of backups by defining a robust strategy
When dealing with an Active Directory compromise, the unavailability of backups (corrupted or compromised) is a major challenge. Attackers frequently target and disable backups or disrupt backup servers. This complicates and lengthens Active Directory restoration and recovery.
Before the crisis…
Create a resilient backup strategy that takes best practices and recommendations into account (backup on disconnected media, immutable or in the cloud) [2]. There is currently a significant gap between state-of-the-art and implemented backup strategies (for example, Active Directory authentication of backup infrastructures, unsecured domain controller backups, and so on).
During the crisis…
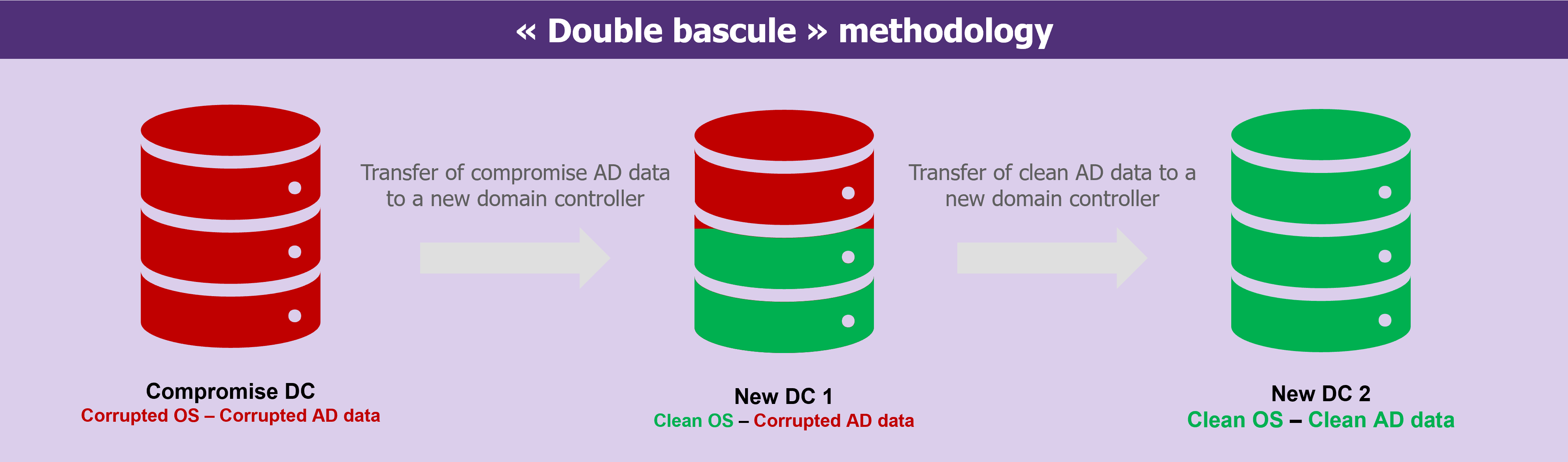
Consider performing Active Directory remediation from a compromised domain controller. This “double bascule” method can assist in recovering and securing critical data in order to restore the Active Directory service without the use of a backup. When backups are unavailable and the strategy does not include rebuilding Active Directory from scratch, this scenario is selected.
Anticipate technical problems such as DNS Active Directory configuration by maintaining your environment
The vast majority of Active Directory environments have accumulated technical debt over time (complex network architecture, roles such as DHCP carried out by domain controllers rather than dedicated servers, and so on). Furthermore, Active Directory environments are now synchronised with Azure Active Directory, establishing new technological dependencies that may complicate remediation in the event of an Active Directory compromise (Active Directory/Azure Active Directory synchronisation). These two elements can cause an array of technical issues on the day of the crisis (loss of synchronisation with Azure Active Directory, unavailability of the DHCP service carried by a domain controller that must be turned off, and so on).
Before the crisis…
Maintain Active Directory technical documentation and inventories (infrastructure, Azure Active Directory synchronisation, etc.). It often proves too difficult to obtain a clear view of the environment and the perimeter to be remediated. Up-to-date inventories will significantly improve remediation work and ensure the establishment of a consistent remediation plan. Additionally, this will allow you to identify and correct bad practises that could cause major issues on the day of the crisis (DNS service configuration, DHCP, and so on).
During the crisis…
After 30 days of desynchronization with the Active Directory, Azure Active Directory services may become unavailable, resulting in a ticking time bomb. Make sure to assess the consequences of losing Azure Active Directory services and avoid relying on them to handle critical tasks (email communication, for example).
The crisis will highlight numerous technical flaws (Active Directory configuration report via audit tools, network issues, and so on). Make sure to only deal with problems that are related to the remediation plan’s objectives (see Advice No. 5 – Set a course and stick to it during remediation!).
Optimize the reinitialization of secrets through processes adapted to your context
Active Directory compromise results in a loss of trust in all of its secrets. As such, a reset of these is required to achieve the level of security required to reopen services while avoiding another quick compromise. Resetting a large number of user passwords and service accounts can have significant operational consequences in large environments with several thousand users and more than a hundred applications. To provide the new password for service accounts, you must first understand how the application uses the account. For users, you must devise a secure method of distributing new passwords on a large scale.
Before the crisis…
It is critical to have a clear understanding of the process of assigning new passwords to users. Several methods are available, depending on the environment studied, such as summoning users with the presentation of an identity card, transmitting the new username/password via physical mail, email, SMS, and so on. Regardless of the method chosen, the user must be required to reset his password on the next connection. Users may also be able to reset their own passwords using solutions that rely on two-factor authentication, for example.
To carry out service account work, it is essential to create an inventory by identifying the associated applications and password reset methods for each of them. Obtaining this inventory by remediation teams is frequently complicated (unavailable, not maintained, etc.) and thus necessitates devoting significant time to tasks that can be completed outside of the crisis. Aside from remediation work, this exercise will help you manage your service accounts on a daily basis. One of the best practices is to change the passwords on these accounts on a regular basis.
During the crisis…
Once the passwords have been reset, it is necessary to ensure that the security measure has been implemented throughout the environment. This is easily accomplished with a PowerShell script, and it ensures that the attacker no longer has a valid account to exploit.
Set a course and stick to it during the remediation!
During an Active Directory reconstruction, it is frequently difficult to strike the right balance between exposing oneself to risks by reopening too quickly and incurring significant financial losses by reopening too slowly. Take care not to fall into the common pitfalls of managing a ransomware crisis.[3]
Before the crisis…
It is necessary to consider the various remediation postures: quickly restoring vital services, regaining control of the information system, or seizing the opportunity to prepare for long-term control of the information system. [1]
Beyond defining the posture, ensure that you understand your Active Directory trust core, which is made up of the most critical assets (Tier 0). The remediation actions begin with these components (domain controllers, for example) in order to restore Active Directory’s vital services and to ensure a level of security that does not allow the attacker to compromise the entire environment again.
During the crisis…
Make sure that your teams stay on track. As the remediation plan is carried out, new issues will emerge (unavailability of the domain controller carrying one of the required FSMO roles for remediation, network problems, and so on). It will be necessary to question the short-term relevance of its remediation in relation to the set objectives (the answer being dependent on the executive committee’s posture: quick reopening or slower and more secure).
Consider the opportunities presented by the crisis. For example, if the DHCP service was managed by a domain controller, take advantage of the opportunity to set up a dedicated DHCP server, thereby decoupling the service from the domain controller.
Our lessons

The improvement of the reconstruction process before the compromise of Active Directory ultimately rests on three main axes:
- The drafting of functional processes and reflex cards to be able to:
- Mobilize the right people in a timely manner.
- Focus on the main objectives.
- The maintenance of the Active Directory environment, which requires:
- Defining and maintaining an architecture in accordance with best practices.
- Having up-to-date inventories.
- Ensuring the resilience of backups.
- The performance of tests to:
- Validate the applicability of theoretical processes in real conditions.
- Improve the reactivity and efficiency of your teams in a crisis situation.
[1] https://www.ssi.gouv.fr/actualite/lanssi-publie-pour-appel-a-commentaires-un-corpus-documentaire-sur-la-remediation/
[2] https://www.riskinsight-wavestone.com/en/2023/02/approaches-to-quick-active-directory-recovery/
[3] https://www.riskinsight-wavestone.com/en/2023/01/successful-ransomware-crisis-management-top-10-pitfalls-to-avoid/


