This year again, we were delighted to be able to share our knowledge during Hacker Summer camp (cybersecurity conferences that happen roughly at the same time in Las Vegas each year: BlackHat, BSides Las Vegas, and DEFCON). (Thomas is…
Category: Focus
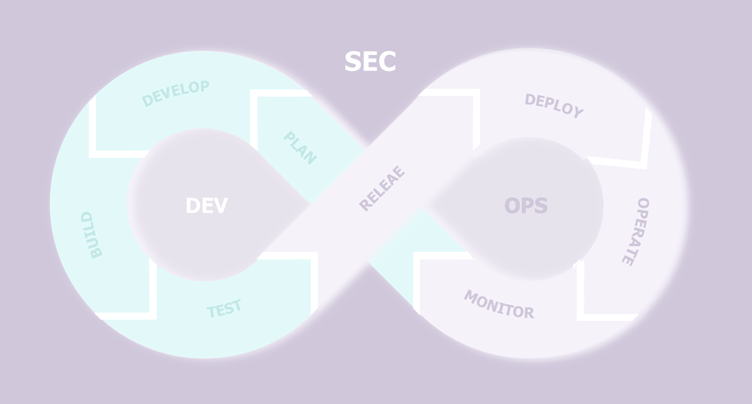
Is it necessary to engage in DevSecOps because projects work in Agile? A few questions need to be asked to get a clearer picture. In previous articles, we talked a lot about how security should be organised to accompany agile…
Today, many companies have initiated a migration to the public cloud, and this brings its share of benefits, but also new attack surfaces. In this article, we will look at how companies can best manage their security posture, by verifying…
The use of "guest" identities to facilitate collaboration externally The need for collaboration externally entails risks for companies Companies have always needed to collaborate with each other by sharing resources and exchanging data. To do this, their collaborators must…
Active Directory (AD) is a directory provided by Microsoft since Windows 2000 Server, that centralises the mechanisms for identifying, authenticating, and managing access rights to the organisation's resources. This component is adopted by a significant number of organisations (approximately 90 to…
The multiple perks of establishing a cyber budget management For the past few years, companies have seen their cybersecurity budgets significantly increasing; according to the latest Gartner reports, they have increased by 51% since 2018. Chief Information Security Officers…
Cyber issues in the energy sector The energy sector is made up of vital infrastructures and provides essential services for a country. The sector, shaped by increasing digitalization, is undoubtedly a prime target for cyber attackers with consequences that are liable…
I often talk about cybersecurity awareness: I share concepts and best practices, but today I'm writing from another point of view: that of the person who has been made aware! Yes, experts are not exempt from awareness initiatives... let me…
Backup security is a topic of increasing concern to large accounts, often as part of initiatives to improve their cyber-resilience. When all the protection, detection and response measures have not been sufficient: the information system must be restored quickly from…
Using passwords introduces both a large attack surface (phishing, brute force, password spreading, rainbow table, etc.) and a poor user experience. As a result, passwords have been denounced in favour of passwordless technologies for several years. However, passwords remain commonly…