Feedback on AWS and Azure Misconfigurations in cloud environments are still a source of major incidents and will keep on reoccurring endlessly. With the news continuously providing new examples: leakage of 1 billion citizens' data linked to a key leak,…
Category: Cloud & Next-Gen IT Security
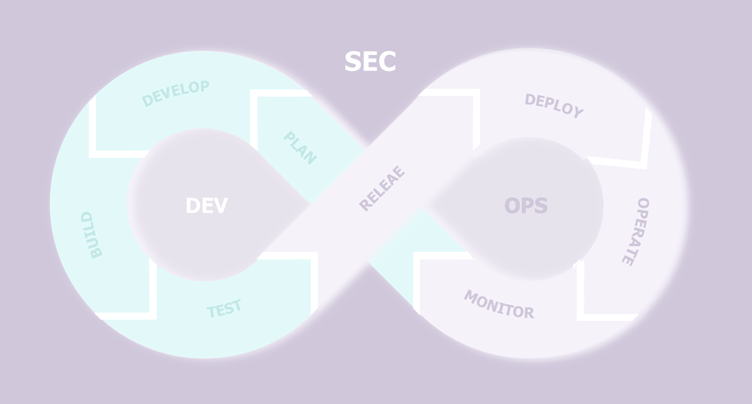
Is it necessary to engage in DevSecOps because projects work in Agile? A few questions need to be asked to get a clearer picture. In previous articles, we talked a lot about how security should be organised to accompany agile…
Today, many companies have initiated a migration to the public cloud, and this brings its share of benefits, but also new attack surfaces. In this article, we will look at how companies can best manage their security posture, by verifying…
The use of "guest" identities to facilitate collaboration externally The need for collaboration externally entails risks for companies Companies have always needed to collaborate with each other by sharing resources and exchanging data. To do this, their collaborators must…
Since the beginning of its theorisation in the 1950s at the Dartmouth Conference[1] , Artificial Intelligence (AI) has undergone significant development. Today, thanks to advancements and progress in various technological fields such as cloud computing, we find it in various…
Active Directory (AD) is a directory provided by Microsoft since Windows 2000 Server, that centralises the mechanisms for identifying, authenticating, and managing access rights to the organisation's resources. This component is adopted by a significant number of organisations (approximately 90 to…
Vincent, can you tell us about the cloud and the challenges of securing it? First of all, it is important to know that cloud security is particularly different depending on the type of cloud and the way cloud services are…
Roxane, could you please introduce us with the operational resilience management? Dashboards and KPIs that convey concrete messages and calls for action are often what drives the success of operational resilience initiatives. Operational resilience brings together and harmonises multiple disciplines…
In 2013, the FBI issued a Stored Communications Act warrant for emails stored in Ireland, on one of Microsoft’s datacenters as part of a drug trafficking investigation. Microsoft refused to provide this information, because the data in Ireland is beyond…
If 10 years ago, building your SOC meant asking yourself which scenarios to monitor, which log sources to collect and which SIEM to choose, recent developments in the IS have brought new challenges: how to set up monitoring in…